
How Istio ambient mode will accelerate Istio rollout for our customers
In April 2025, the ACA Cloud team visited Kubecon + CloudNativeCon 2025 in London. In this blog, we dive into the key takeaways from the conference, focussing on Istio ambient mode, and how it will significantly simplify and accelerate Istio adoption for ACA and our customers.

What is Istio?
Istio acts as a proxy between the different applications (services) within a Kubernetes cluster, ensuring that every request flows through a component of Istio. This layer, responsible for communication between all applications, is called a service mesh.
Istio provides traffic management, security, observability and simplified communications for all of the applications within the cluster.
Traffic management
Istio enables detailed traffic management, allowing developers to easily route, distribute, and control traffic between different versions of their services.
Security
With built-in mTLS encryption, Role-Based Access Control (RBAC), and centralized authentication policies, Istio ensures secure communication between services—without needing to manage certificates or security logic at the application level.
Observability
Through built-in instrumentation, Istio offers metrics, logs, and traces, providing deep visibility into how services perform and interact. This allows IT teams to quickly identify bottlenecks and debug issues in complex environments.
Simplified communication
By abstracting service-to-service communication, Istio removes networking concerns from application code. Developers can focus on features, while the mesh handles routing, security, and reliability behind the scenes.
Want to know more about Istio? Check our other blogs:
- Istio Service Mesh: What and Why
- How to Install Istio Service Mesh: A Comprehensive Step-by-Step Guide
For all official Istio documentation, go to https://istio.io/latest/.
Istio’s current design and its limitations
Istio ensures that every request within the cluster passes through one of its components (the envoy proxy). This allows Istio to inspect, manage and secure all requests. It's essential for enabling features like request tracing and enforcing encryption between services.
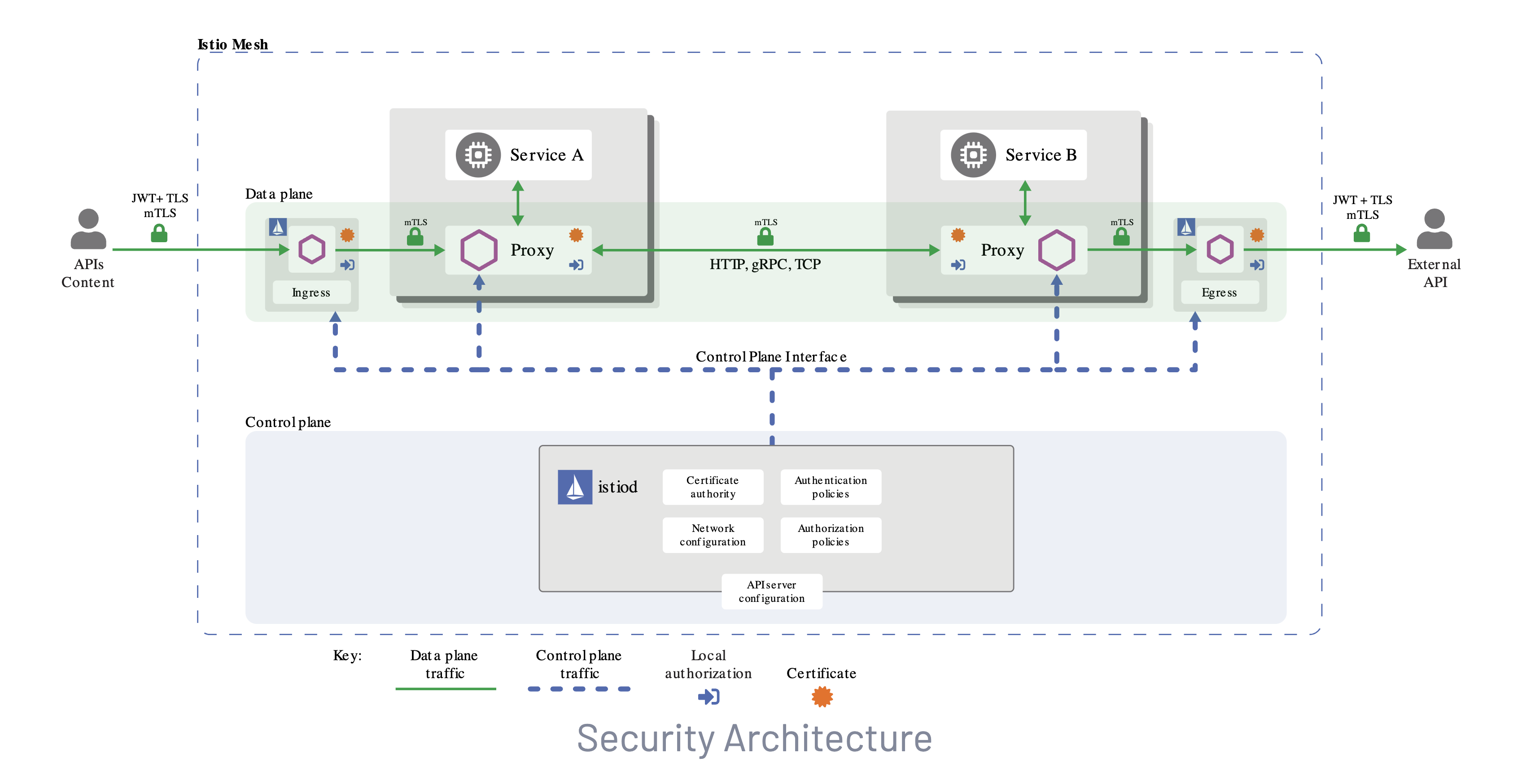
A request that uses all components follows this path :
- Traffic enters via the ingress gateway.
- The ingress gateway forwards traffic to the sidecar proxy of application 1 (Service A).
- Traffic passes through the sidecar proxy of application 2 (Service B)
- Traffic exits via the egress gateway.
All gateways and proxy sidecars are running the envoy proxy. The sidecar envoy proxy containers are running within the Kubernetes pod for each application.
Downside of the sidecar model
Istio is an interesting tool that offers a lot of added benefits, but the current sidecar model does have a few downsides:
- High resource usage: Every pod runs its own Envoy proxy
- Complex updates: Any proxy change requires pod restarts
- Kubernetes Jobs incompatibility: Sidecars don’t shut down with job completion
- Same resource config: Can’t fine-tune proxy resource per application
Despite the above limitations, ACA has successfully deployed Istio in a few customer environments. And with a redesign, a lot of these concerns might be resolved.
Added value of Istio for ACA and its customers
Before we get into the details of the redesign with ambient mode, let us explain which Istio features we use most and why.
Traceability and observability
Istio enables end-to-end request tracing, helping us:
- Visualize service flows
- Monitor versions of deployed applications
- Identify bottlenecks and performance issues
Strong cluster-wide security
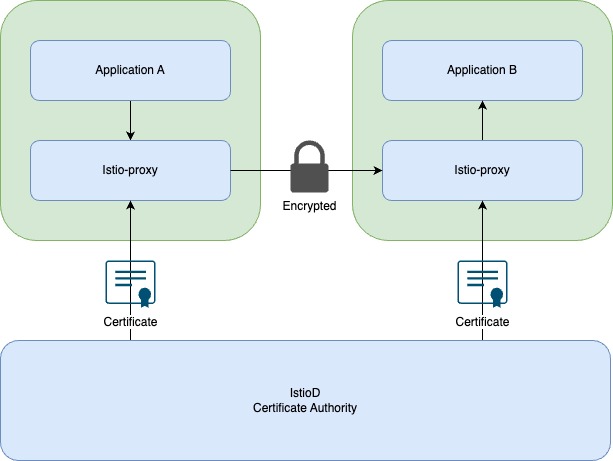
Most setups and implementations for non-Istio clusters require reconfiguration and managing certificates on an ingress-controller and application level. Using Istio, all pod-to-pod and node-to-node traffic is encrypted by default. This meets regulatory standards (like NIS2) and prevents the need for custom TLS setups in every application.
Simplified authentication
Istio also simplifies our development flow. For one of our customers, we moved all authentication configuration to Istio using RequestAuthentication objects. Istio will handle authentication with Auth0 using jwt tokens. This means developers don’t need to handle authentication in the application, which leads to less code and faster development. On top of that, Istio takes care of authentication in a consistent way across all services.
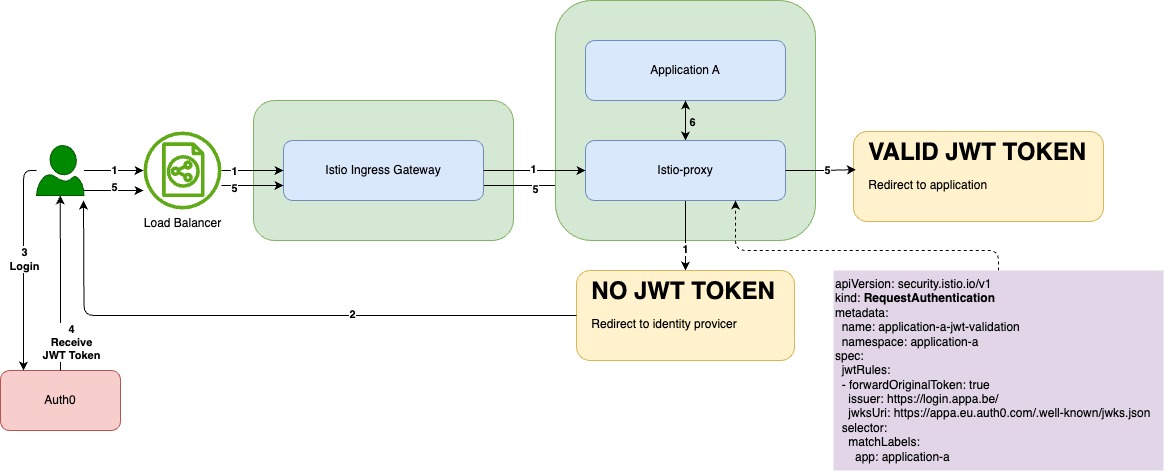
Future-proof traffic control
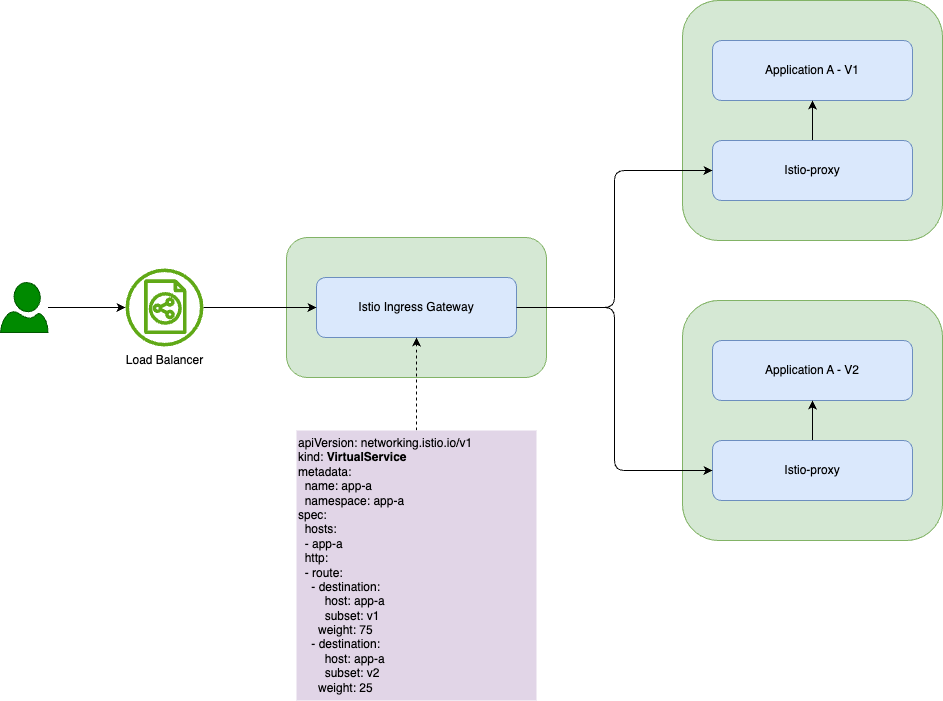
Istio also offers additional features for traffic control, like:
- Blue/green deployments
- Feature flags
- Weighted routing
Although we have not used this features yet, it is convenient to have them in place as needs evolve.
Introducing ambient mode: the future of Istio
As mentioned above, the current sidecar model of Istio comes with a few downsides.
The goal of ambient mode is to create a new architecture where a new layer is added, that replaces the sidecars.
What is Istio ambient mode?
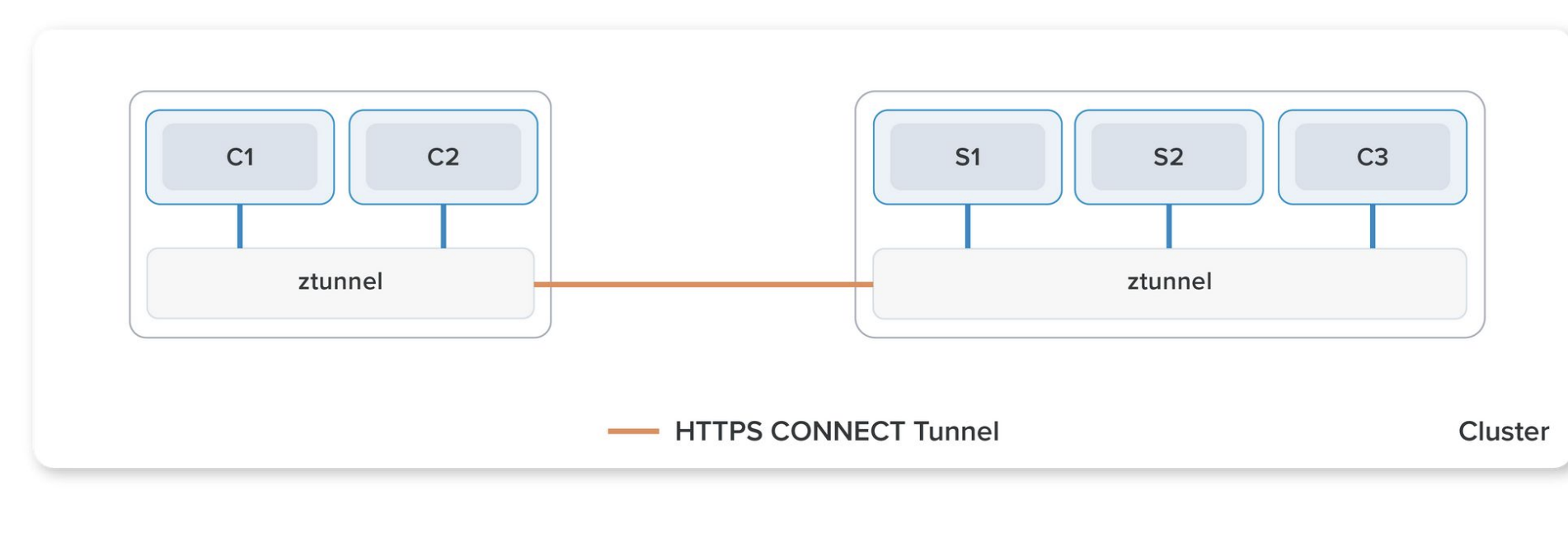
Ambient mode introduces a ztunnel (Zero Trust Tunnel), running on each Kubernetes node. It manages:
- mTLS encryption
- Basic L4 traffic policies (authn, authz, telemetry)
All traffic will flow through this layer, even if the traffic goes to a container on the same node.
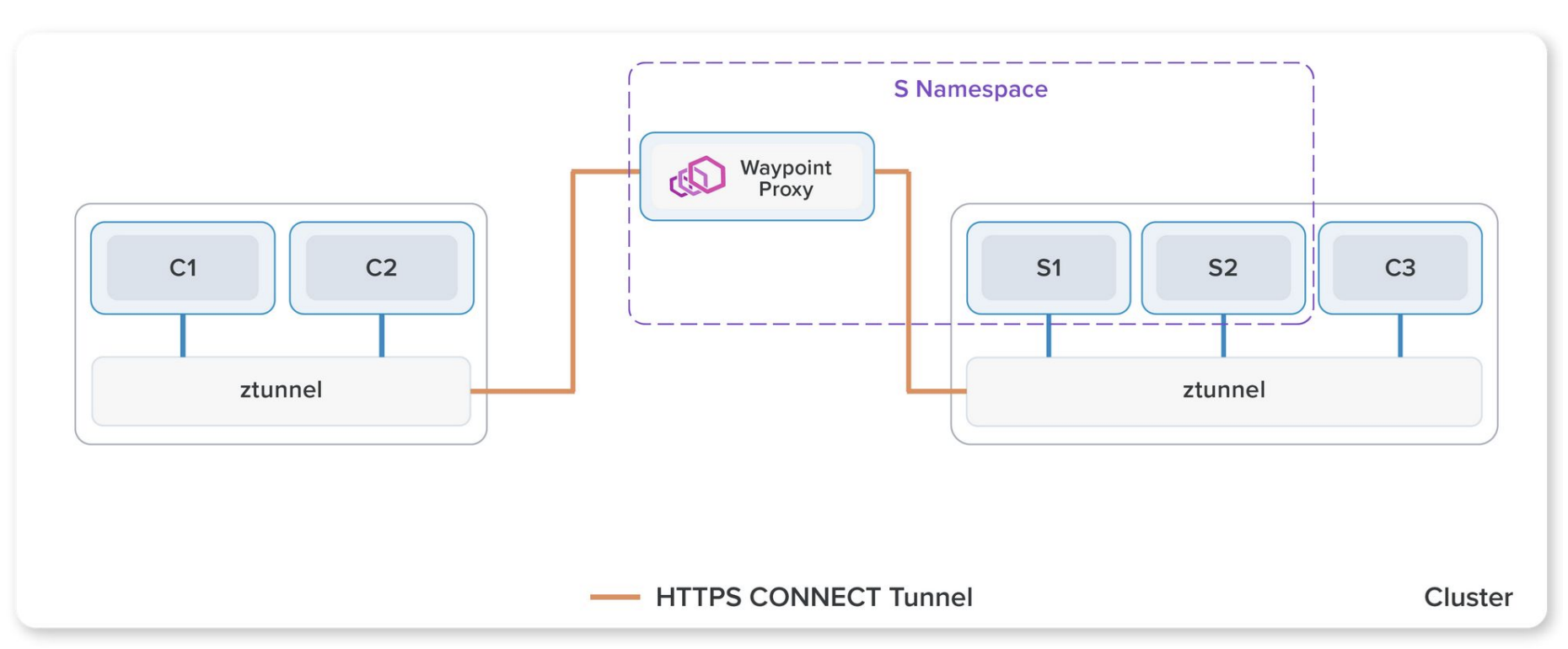
If you need Layer 7 features like advanced traffic control, you’ll also need to deploy a waypoint proxy. This is an envoy proxy that handles the same advanced traffic management tasks as the traditional sidecar mode.
Same features, easy updates
Ambient mode uses fewer resources and decouples Istio from the applications themselves. As a result, changes like upgrades or configuration updates no longer require application restarts. Even better, ambient mode still provides the same powerful features we had with sidecar mode.
Shifting from sidecars to ambient mode
While ambient mode is a promising step forward, it’s still under active development. The traditional sidecar setup remains fully supported, and not all features have been migrated yet. For the most up-to-date status, check Istio’s official documentation.
We’re excited to begin transitioning our current environments to ambient mode and to roll out Istio in clusters that haven’t yet adopted a service mesh. Stay tuned—we’ll be sharing more updates on our journey soon!
Curious how Istio ambient mode could benefit your environment?
Whether you're considering Istio for the first time or looking to modernize your current setup, our cloud experts are happy to explore the possibilities with you.


