
Integrating NIS2 practices in Azure
Cybersecurity is no longer optional—it’s a cornerstone of every organization’s operational resilience and compliance strategy. With the introduction of the EU's NIS2 directive, European organisations face a pressing need to meet rigorous security standards. While the EU's NIS2 directive sets clear standards for network and information security, translating its mandates into actionable steps can be a challenge—especially for businesses using cloud platforms like Microsoft Azure.
Fortunately, Azure offers a range of tools designed to simplify compliance and strengthen your security framework. In this post, we’ll explain how Azure can help you to align with NIS2, breaking down the process into manageable steps to help you secure your environment and stay compliant.
What is NIS2?
The EU’s NIS2 (Network and Information Security Directive 2) is a cybersecurity directive introduced by the European Union to enhance the resilience and security of critical infrastructure and essential services across member states. It replaces the original NIS Directive from 2015 and has been incorporated into the national laws of each EU member state since October 18th, 2024.
NIS2 standardizes cybersecurity practices for a wide range of sectors and organizations, from digital services, healthcare and energy, to transportation and public administration. Non-compliance can result in high fines and even reputational damage, so for affected organizations adherence is crucial.
Challenges of NIS2
NIS2 covers a broad range of cyber security objectives, including governance, risk management and incident response. With so many objectives, it can be a daunting task for organisations to translate them into actionable steps.
Are your infrastructure resources located in the public cloud Azure? Do you know Azure offers important tools in order to audit and ensure your environment is NIS2-compliant.
How to start the implementation of NIS2?
The first step for implementing NIS2 is to break the directive into smaller manageable controls. Once this has been done, the work of mapping the controls to the best technology and process can start.
In this blog, we will break down a specific set of controls and map them to a technology with a focus on Microsoft Azure and Microsoft Entra ID.
 Microsoft Entra ID: identity and access management for NIS2 compliance
Microsoft Entra ID: identity and access management for NIS2 compliance
One of the core requirements of NIS2 is ensuring only authorised personnel have access to critical systems and data. With Microsoft Entra ID, you have a very robust set of identity and access management (IAM) tools.
Multi Factor Authentication
Multi Factor Authentication (MFA) has become the de facto standard security method. It requires a user to provide at least two verification factors to access the environment.
Conditional Access Policies
Conditional Access Policies are often overlooked because they seem optional, but they are essential for ensuring a secure environment. They define the conditions users must meet to access the environment. They may grant or deny access based on parameters such as:
- IP address (location)
- User Group Membership in Entra ID
- Device Posture and compliance
Just-in-Time Access
Additional safety measures such as Just-in-Time-Access, which grants specific rights for a limited time, should also be configured. As an administrator, you should maintain read-only access by default, using Just-In-Time-Access to temporarily elevate privileges during approved change windows.
Security Information and Event Management
All the safety measures in the world mean nothing if you don’t have an effective way to continuously monitor and respond accordingly. There are several SIEM (Security Information and Event Management) solutions available. You can adopt Microsoft Sentinel which has both hybrid and cloud native support.
 Microsoft Sentinel
Microsoft Sentinel
At ACA, we recommend closely monitoring your secure score in Microsoft Entra ID tenant. It provides a quick, clear overview of your compliance progress.
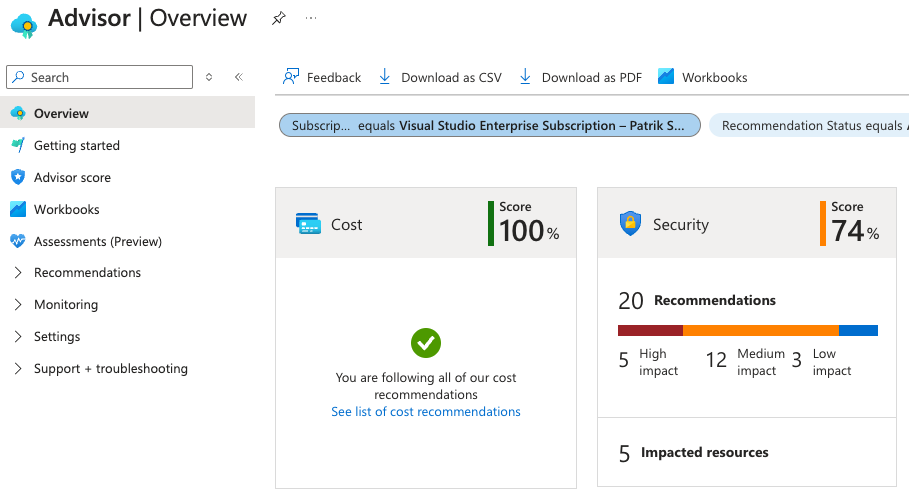
 Azure tools for NIS2 compliance
Azure tools for NIS2 compliance
The Azure platform provides many tools and technologies to help you with NIS2 compliance.
Microsoft Defender for Cloud
Microsoft Defender for Cloud is an excellent tool to provide real-time threat detection along with security recommendations for different Azure resources such as VM’s, SQL databases, storage and many more. This also includes monitoring for vulnerabilities, policy compliance and security misconfigurations.
Azure policy
Azure policy is the foundation for keeping your infrastructure compliant, establishing the foundations of your governance framework for your entire landing zone.
Before provisioning your first workloads in Azure, ensure your Azure policies are configured and compliant with the NIS2 directive.
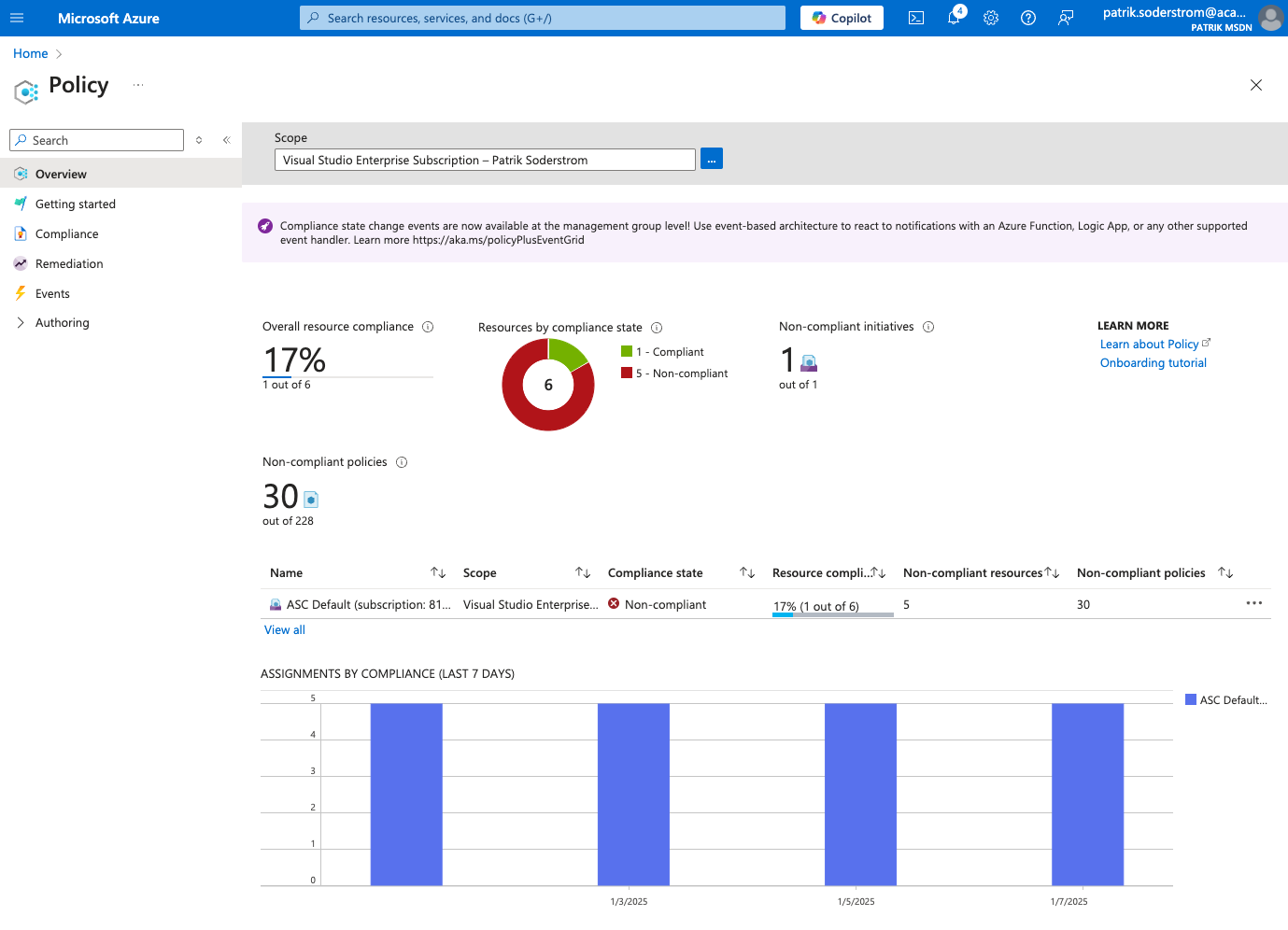
Do you already have workloads in Azure? It makes policy enforcement a little bit more complex, as they are often set up without strict enforcement. In such cases, the policies have to run in ‘audit’ mode. This is where any non-compliance is flagged but not enforced. This approach lets organizations review and assess the impact before fully enforcing policies.
How to manage response and recovery in NIS2?
NIS2 is not only about security, but also has a compliance section on “Response and Recovery”. This is where you can leverage Azure Backup, Azure Site Recovery and of course, Infrastructure as Code.
Focusing further on the actual data, we need to consider the different types of data confidentially. Encryption is key here as it ensures that your data is only accessible to authorized individuals and systems.
There are three main types of encryption available:
1. Data at Rest
When you store a file in an Azure Storage Account, this is encrypted using Service-side encryption (SSE) automatically. There are different types of encryption at Rest in Azure, depending on which service you use.
2. Data in Transit
When data is transmitted over the network there are different ways to encrypt it with the most common being Transport Layer Security (TLS). This is the primary method used when connecting to and interacting with Azure services.
3. Data in Use
Data used for processing, such as when stored in memory, can also be encrypted. This is oftentimes overlooked because it’s more complex and the implementation varies depending on which service you use. If you use virtual machines in Azure, there’s a whole area covering Confidential Computing. In case someone would try to read the memory of the host, it is encrypted and unreadable.
Struggling with NIS2 compliance?
The journey towards NIS2 compliance is exciting, but can also be complex. The technological aspects alone involve numerous controls across various public cloud technologies. However, achieving true compliance requires a balanced approach that integrates the technologies with robust processes and governance.
➡️ At ACA, we care deeply about security. Wherever you are in the NIS2 journey, you can count on us to guide you towards NIS2 compliance success.
Questions about NIS2 compliance?


